Radio Frequency Identification (RFID) technology has become integral to our daily lives, enabling contactless payments, access control, and efficient inventory management. While these conveniences are beneficial, they come with significant security risks, especially the potential for RFID skimming. This comprehensive guide will explore the risks associated with RFID, including what is RFID blocking as a solution, determine if RFID-blocking solutions are effective, examine how devices like the Flipper Zero can be misused for skimming, and provide practical solutions to safeguard your personal information.
What is RFID Skimming?
RFID skimming is a form of digital theft where unauthorized individuals use specialized devices to access and extract information from RFID-enabled cards and devices without the owner’s consent. RFID (Radio Frequency Identification) technology is commonly found in contactless credit cards, identification cards, passports, and key fobs, enabling quick and convenient data transmission over short distances.
In an RFID skimming attack, malicious actors employ handheld RFID readers or skimming devices that can intercept the wireless signals emitted by these cards. These devices can capture sensitive information, such as card numbers, expiration dates, or personal identification details, even if the card is tucked inside a wallet or bag.
Such attacks are particularly concerning because they can occur without any physical contact, often going unnoticed by the victim. This stealthy nature makes RFID skimming a serious threat to privacy and data security. Although RFID technology is designed to work only within a limited range—typically a few inches—advanced skimming devices can sometimes increase this range, further exacerbating the risk.
The potential consequences of RFID skimming include financial fraud, identity theft, and unauthorized access to secure facilities or systems. As a result, individuals and organizations have become increasingly aware of the need for protective measures, such as RFID-blocking wallets and card sleeves, to safeguard their information from this form of digital theft.
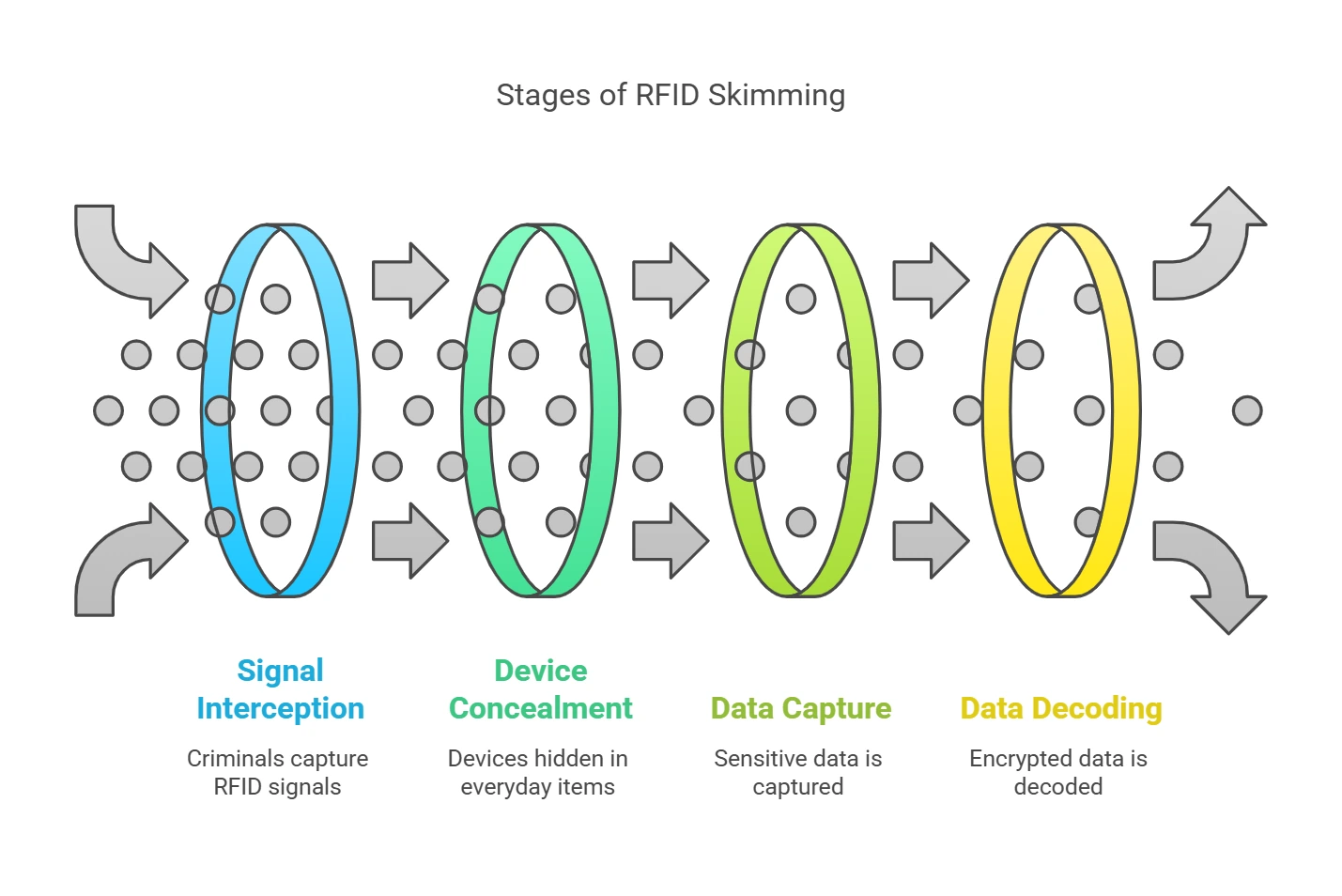
How RFID Skimming is Performed
RFID technology facilitates the wireless exchange of information through electromagnetic fields, transmitting data between RFID-enabled cards and compatible readers without direct contact. While convenient, malicious actors can also exploit this functionality to perform RFID skimming.
In an RFID skimming operation, a criminal uses an RFID reader or scanner to intercept the radio signals emitted by RFID-enabled cards. These readers are programmed to mimic legitimate devices, tricking the card into transmitting sensitive information. The range of standard RFID communication is relatively short—typically a few inches to a few feet—but criminals may use enhanced equipment to extend this range, increasing the risk.
Attackers often embed RFID scanners to conceal their intent within everyday objects such as bags, jackets, or gloves. This allows them to carry the device inconspicuously in crowded areas like public transport, shopping malls, or airports, with higher proximity to potential victims. With just a brief moment of closeness—sometimes as quick as walking by—the skimming device can capture crucial details such as card numbers, expiration dates, or other encoded data.
Some advanced skimming setups also utilize software to decode encrypted RFID signals, potentially gaining access to even more secure systems. Additionally, the portability and affordability of RFID readers make them accessible to a broader range of individuals, further complicating efforts to curb such attacks.
The covert and contactless nature of RFID skimming underscores the importance of staying vigilant and adopting preventative measures, such as using RFID-blocking wallets, card sleeves, or secure transaction alternatives.
Incidence of RFID Skimming
Reports suggest that there was a noticeable increase in card-not-present fraud from 2012 to 2016, some of which have been linked to RFID skimming. However, accurately quantifying the prevalence of RFID skimming remains challenging due to its highly covert nature. Unlike traditional forms of theft, such as ATM skimming or physical card theft, RFID skimming often leaves no tangible evidence behind, making it difficult for victims to identify the source of fraudulent activity.
Many incidents attributed to card-not-present fraud involve the unauthorized use of payment card details obtained through various means, including RFID skimming. However, due to the lack of clear forensic markers, differentiating RFID-based theft from other methods, such as phishing or data breaches, is complex.
Furthermore, reported cases of RFID skimming are significantly lower than other forms of theft, partly because financial institutions and security experts have implemented measures to mitigate these risks, such as EMV (Europay, Mastercard, and Visa) chip technology and tokenization. These advances have reduced the susceptibility of newer cards to skimming-related exploits.
Despite the relatively low number of reported incidents, the potential for RFID skimming remains a concern, particularly in environments where older RFID-enabled cards or devices are still in use. Public awareness campaigns, improved technology, and increased availability of protective accessories, such as RFID-blocking wallets, have played a significant role in curbing the impact of RFID skimming.
While the exact incidence of RFID skimming is difficult to determine, the threat underscores the need for continued vigilance, mainly as evolving technologies may introduce new vulnerabilities.
Do RFID Blocking Solutions Work?
In response to the growing concerns surrounding RFID skimming, a variety of RFID-blocking solutions, such as wallets, sleeves, and even apparel, have emerged to safeguard RFID-enabled cards. These products create a physical shield that blocks or disrupts electromagnetic signals, effectively preventing unauthorized communication between RFID readers and the cards they are designed to protect.
The primary mechanism behind RFID-blocking solutions involves using materials like aluminium or metal-infused fabrics that can absorb or reflect the electromagnetic waves emitted by RFID readers. When a card is enclosed within an RFID-blocking wallet or sleeve, the shield acts as a Faraday cage, a structure that prevents electromagnetic fields from penetrating and interacting with the card’s chip.
Studies and consumer tests have demonstrated that high-quality RFID-blocking products effectively prevent unauthorized scanning under most conditions. However, their efficacy can vary depending on factors such as the RFID reader’s strength, the blocking material’s quality, and the frequency at which the card operates. Most RFID-enabled cards today, such as contactless credit cards or identification cards, operate within standard frequency ranges (typically 13.56 MHz), which are well-protected by these solutions.
While RFID-blocking wallets and sleeves provide an added layer of security, it is worth noting that the risk of RFID skimming is relatively low compared to other forms of card fraud. Many modern cards incorporate additional security features, such as encrypted communication and dynamic data authentication, which minimize the likelihood of successful skimming.
Despite these advancements, RFID-blocking products remain popular for consumers seeking peace of mind, especially in high-traffic areas like airports or public transport, where the risk of close proximity attacks is higher. These solutions are practical and cost-effective, making them a worthwhile investment for individuals concerned about their digital and financial security.
Effectiveness of RFID Blocking Technologies
Research consistently demonstrates that many RFID-blocking products are effective at preventing unauthorized access to RFID-enabled cards. For instance, a study conducted by ZDNet tested various RFID-blocking technologies and found that high-quality RFID-blocking cards successfully disrupted signals, even when layered behind or between other cards. This underscores the effectiveness of these products in real-world scenarios where multiple cards are carried together.
The core principle of RFID-blocking technologies lies in their ability to create a shield that absorbs or reflects electromagnetic waves. Products such as RFID-blocking wallets, sleeves, and cards are typically made from conductive materials like aluminium or copper that neutralize the reader’s signal before it can interact with the RFID chip.
However, the effectiveness of these solutions varies significantly among different products. Independent tests have revealed that some lower-cost or poorly designed products may provide insufficient protection, allowing certain signals to penetrate under specific conditions. For instance, thinner materials or improperly sealed sleeves might fail against stronger RFID readers or prolonged attempts to scan.
Interestingly, simple, low-tech solutions such as wrapping RFID-enabled cards in aluminium foil have achieved similar results to some commercial RFID-blocking products. This has led to debates about the necessity of specialized items, though commercial options often offer better durability, convenience, and style.
While RFID-blocking technologies are highly effective against unauthorized scans, it is essential to contextualize their necessity. The actual risk of RFID skimming remains relatively low due to advancements in card security, such as encryption and dynamic verification. Nonetheless, investing in reliable RFID-blocking solutions provides an added layer of peace of mind for those seeking extra assurance, especially in crowded or high-risk environments.
Is RFID Blocking Necessary?
The necessity of RFID-blocking technology is a topic of ongoing debate among security experts and consumers. While RFID skimming is theoretically possible and has been demonstrated in controlled environments, real-world instances of individuals being successfully targeted are relatively rare.
One primary reason for the low incidence of RFID skimming is the advancement of security measures in modern RFID-enabled cards. Most contemporary contactless credit cards, passports, and identification cards incorporate robust encryption protocols and dynamic data authentication. These features generate unique, one-time codes for each transaction, rendering stolen data nearly useless for fraud.
Additionally, financial institutions and card issuers have implemented fraud detection systems that monitor transactions for unusual activity, further mitigating the risks posed by RFID skimming. As a result, the likelihood of falling victim to this specific type of theft is significantly lower than other forms of fraud, such as phishing or traditional card theft.
However, factors such as individual risk tolerance and situational context influence the debate over the necessity of RFID blocking. For example, frequent travellers or individuals who spend time in densely populated areas, where proximity scanning is more feasible, may find RFID-blocking solutions a worthwhile investment for added peace of mind.
While the need for RFID-blocking technology may not be universal, it can serve as a precautionary measure, particularly for those who value an extra layer of protection against potential threats. For others, the existing security features of modern cards may provide sufficient reassurance, making RFID blocking a less critical concern.
The Role of Flipper Zero in RFID Skimming
The Flipper Zero is a compact, versatile device interacting with various electronic systems, including RFID, NFC, infrared, and wireless signals. Initially developed as an educational tool for hobbyists and cybersecurity enthusiasts, it allows users to explore and experiment with digital protocols in a controlled environment. However, its ability to read, emulate, and manipulate RFID signals has raised concerns about its potential misuse in RFID skimming and other unauthorized activities.
One of Flipper Zero’s key features is its capability to read RFID cards operating at standard frequencies, such as 125 kHz and 13.56 MHz. This functionality allows users to store and emulate RFID tags, granting access to systems like door locks, security gates, or payment terminals. While this capability is invaluable for legitimate uses, such as testing the security of RFID-enabled systems or replacing lost tags, it also opens the door for exploitation by malicious actors.
The device’s portability and user-friendly interface make it appealing to individuals with malicious intent. For example, in the hands of an attacker, the Flipper Zero could be discreetly used in crowded areas to read and clone RFID-enabled cards from unsuspecting individuals. This has sparked debates in the security community about the ethical implications of such powerful tools being easily accessible.
It is important to note that the developers of Flipper Zero discourage misuse and promote ethical use through educational content and community guidelines. However, as with any tool, the user is responsible for ensuring that it is used within the bounds of the law and ethical standards.
The emergence of devices like the Flipper Zero underscores the need for heightened awareness and robust security measures. As technology advances, individuals and organizations must remain vigilant, adopting modern security solutions such as encrypted RFID systems, two-factor authentication, and physical safeguards like RFID-blocking accessories to protect against potential threats.

Features and Risks
The Flipper Zero boasts impressive features, particularly its ability to read, copy, and simulate RFID and NFC tags. This functionality allows users to interact with various systems, such as access control devices, public transportation cards, and payment systems. Its versatility and compact design make it an attractive tool for security testing and educational purposes.
However, the same features that make the Flipper Zero a valuable tool for ethical applications also make it a potential risk in the hands of malicious actors. With minimal technical knowledge, individuals can use the device to capture and clone RFID tags, potentially gaining unauthorized access to sensitive systems or personal information. For example, an attacker could use Flipper Zero to replicate access cards for secure facilities or clone NFC-enabled payment cards to facilitate fraudulent transactions.
Its accessibility and ease of use amplify the risks associated with Flipper Zero. Unlike traditional skimming devices, which may require advanced technical expertise or significant setup, the Flipper Zero offers a user-friendly interface and readily available community support, lowering the barrier to entry for potential misuse.
While Flipper Zero’s developers emphasize its intended purpose as a learning tool, the device’s potential for abuse raises concerns about consumer safety, especially in public spaces where proximity attacks are more feasible. As a result, individuals and organizations must adopt proactive measures to safeguard their RFID-enabled systems. These measures include transitioning to encrypted RFID technologies, implementing multi-factor authentication, and using physical barriers like RFID-blocking wallets or sleeves to mitigate the risks.
The dual nature of tools like the Flipper Zero highlights the ongoing challenge of balancing technological innovation with the need for security and ethical considerations.
Investigating Potential Misuses
The rise of versatile tools like the Flipper Zero has sparked growing concerns about their potential misuse in compromising RFID security systems. While the device was designed with ethical applications in mind, such as education, security testing, and digital experimentation, its capabilities have reportedly been exploited for nefarious purposes.
One of the Flipper Zero’s most alarming aspects is its ability to interact with RFID systems without any physical contact. This capability allows users to intercept, replicate, or manipulate RFID signals discreetly, posing a significant threat to individuals and organizations. Public spaces, such as transportation hubs, offices, and crowded events, are particularly vulnerable, as attackers can operate the device close to their targets without arousing suspicion.
Reports of misuse include unauthorized cloning of access cards to breach secure facilities, emulating NFC tags for fraudulent transactions, and tampering with electronic systems designed to rely on RFID for identification or access control. These cases underscore the formidable nature of the threat, as they demonstrate how a relatively small, affordable, and widely available device can undermine traditional security measures.
The challenge is further compounded by the ease with which such devices can be programmed and operated. Open-source resources, community forums, and readily available tutorials lower the barrier for individuals to experiment with—and potentially abuse—these tools. This has prompted calls for stricter regulation of devices like the Flipper Zero and greater awareness of their implications.
Addressing the risks posed by such devices requires a multi-faceted approach. On a technological level, organizations must invest in advanced security measures, such as encrypted RFID systems, tamper-resistant tags, and multi-factor authentication protocols. Public awareness campaigns and legal frameworks may help deter misuse while encouraging ethical and educational applications of the technology.
The growing concern over the potential misuse of devices like the Flipper Zero highlights the importance of vigilance, innovation, and responsible use of emerging technologies in an increasingly interconnected world.
Solutions for Preventing RFID Skimming Attacks
Implementing RFID Blocking Technology
Adopting RFID-blocking solutions is an effective first line of defence against the threat of RFID skimming. These products are designed to create a physical barrier that disrupts the communication between RFID readers and RFID-enabled cards, thereby preventing unauthorized data access. RFID-blocking wallets, sleeves, and specialized cards are made with conductive materials, such as aluminium or copper, which absorb or reflect electromagnetic signals.
These solutions benefit individuals who frequently travel or spend time in crowded public environments, where proximity skimming attempts are more likely. By incorporating RFID-blocking products into daily routines, users can significantly reduce the risk of falling victim to unauthorized scanning and data theft.
Additional Precautions
While RFID-blocking products provide an essential layer of protection, combining them with additional precautions can further enhance security:
- Monitor Financial Activity Regularly: Review bank and credit card statements frequently to detect and report any unauthorized charges promptly.
- Enable Online Banking Alerts: Set up real-time transaction notifications to stay informed of suspicious activity.
- Limit RFID Card Exposure in Public Spaces: Avoid using RFID-enabled cards in crowded areas where close proximity attacks are more feasible.
- Adopt Advanced Payment Technologies: Transition to more secure options like EMV (chip-enabled) cards and mobile payment solutions. These solutions rely on encrypted communication and dynamic authentication, making them less vulnerable to skimming attacks.
By implementing these practices, individuals can create multiple layers of defence, minimizing the likelihood of financial or identity theft.
Awareness and Education
Enhancing public awareness about RFID technology and its associated risks is crucial to combating RFID skimming. Many consumers are unaware of the vulnerabilities that RFID-enabled cards may present, particularly older models lacking modern security features.
Educational campaigns can empower consumers with the knowledge to make informed decisions about protecting their personal and financial data. For instance, choosing cards with advanced encryption and security features can reduce the risk of skimming even without RFID-blocking solutions. Raising awareness about simple preventative measures, such as carrying RFID-enabled cards in protective sleeves or wallets, can help deter potential threats.
Organizations, financial institutions, and governments can play a vital role by disseminating accurate information, promoting secure technologies, and encouraging responsible practices. Informed consumers are better equipped to recognize potential risks and take proactive steps to safeguard their information, reducing the overall impact of RFID skimming as a security concern.
Conclusion
While RFID technology provides numerous conveniences, it also introduces security vulnerabilities that require consumer awareness and vigilance. Although the risk of RFID skimming exists, the actual instances are rare, primarily due to robust security protocols. While RFID-blocking products can enhance protection, their effectiveness may vary, necessitating informed choices. Devices like Flipper Zero illustrate the ongoing threat to security in our increasingly digitized lifestyle, emphasizing the need for education and preventive measures against identity theft.



